Packet Length Extractor
If you're having server problems, such as:
- Packet Tokenizer: Unknown switch: xxxx
- Getting disconnected after a few seconds
- NPCs, players and monsters are not recognized by Kore (shown as Unknown)
Then generating a new recvpackets.txt might solve the problem. It's advisable to always extract the recvpackets before running Openkore. The file must be on tables folder.
The network data that the server sends to Kore, is a byte stream. Kore must be able to recognize messages inside that byte stream to be able to do something with it. But the size of the messages can vary from to server to server. Recvpackets.txt contains information about the size of each message, so Kore can correctly split the byte stream into messages.
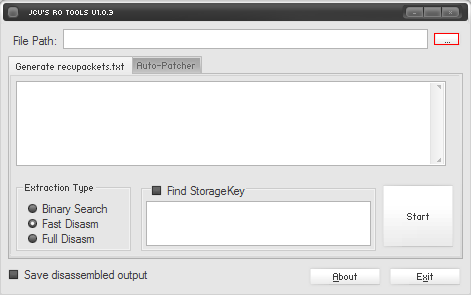
RO Tools
JCV's RO Tools v1.0.3 (See instructions below for OpenPacketExtractor)- Also in OpenKore SVN.
It's better to use JCV's RO Tools as it is more up to date and have some fixes for newer clients. Also it's much easier to maintain, but it has undesirable and outdated options in addition to the Openkore packet extractor.
Usage
- Open RO Tools.
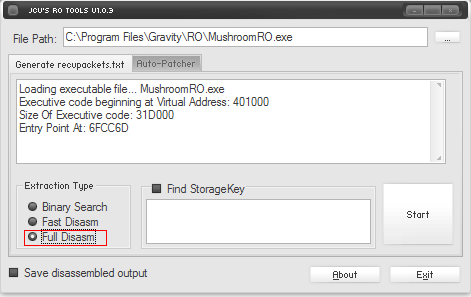
- Click in the button with ... beside the box. Search for your's server executable (not server patcher and not launcher !!!) and open it.
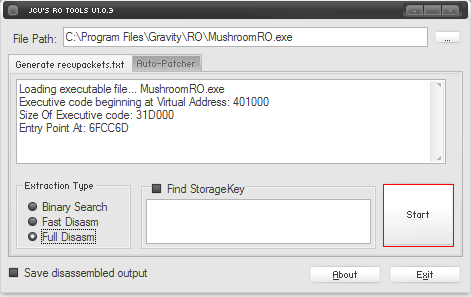
- On Extractor Type, check Full Disarm box.
- Click on Start button and wait it to finish.
- After it finishes, it will ask for you to save the file. Save it on tables folder, inside your Openkore's root folder. Override current file if needed.
Packet Extractor
Usage
- Run
openkore-packet-length-extractor.exe - Click in the button with ... beside the box. Search for your's server executable (not server patcher) and open it.
- Click on Extract button and wait it to finish.
Packet Extractor v3
- Packet Extractor v3
- Mirror: OpenKore SVN. (See kLab's forum post on Open Packet Extractor for more details.)
Packet extractor branch to work with new insert server list here clients.
Usage
Variant 1 (for noobs):
- Download
start.exefrom http://misc.openkore.com and unpack to the same folder wherepacket_extract.plis placed. - Copy target .exe file to the same folder where
packet_extract.plis placed. - Run
packet_extract.batto save extracted packets to text file.
Variant 2 (for profi):
- Download
start.exefrom http://misc.openkore.com and unpack to the same folder where packet_extract.pl is placed (optional). - Copy target .exe file to the same folder where
packet_extract.plis placed. - Run
start.exe ! packet_extract.pl your_exe_name.exeorperl packet_extract.pl your_exe_name.exeto generate "extractor.exe". - Run
extractor.exe > recvpackets.txtto save extracted packets to text file.
Notes
- Recvpackets file can be renamed as long as recvpackets option on servers.txt is set accordingly. (See Connectivity Guide)
- There may be problems extracting the recvpackets if your server's client has some kind of protection. You should deal with it (like unpack if binary is packed) before using packet extractor, if it fails to find anything.